Vendor Risk Assessment: How to Evaluate Third-Party Risks


Businesses often rely on third-party vendors for many services and products. While these partnerships can bring efficiency and innovation, they also pose certain risks to the organization. It can disrupt operational integrity, data security, and compliance.
You should conduct a vendor risk assessment (VRA) to prevent this. This helps you evaluate these risks, make informed decisions, and protect your organization.
In this article, we will uncover the essential components of vendor management risk assessment and how you can do it effectively.
A vendor risk assessment is the process of identifying, assessing, and mitigating risks associated with third-party vendors. It involves scrutinizing a vendor's operations, security practices, financial stability, compliance with regulations, and overall reputation. The primary objective is to uncover vulnerabilities impacting business continuity or regulatory compliance.
A vendor risk assessment should be an integral part of the vendor lifecycle. You should conduct them at the following stages:
Before entering a partnership, it’s crucial to assess the vendor’s risk profile to ensure they meet your operational and security requirements.
Evaluate vendors when renewing contracts or expanding their scope of work. This ensures they remain compliant and capable of handling new responsibilities.
Regular assessments help identify emerging threats and maintain compliance with evolving regulations. A recent survey indicated that in the last 12 months, around 61% of organizations faced a data breach by third parties or other security incidents.
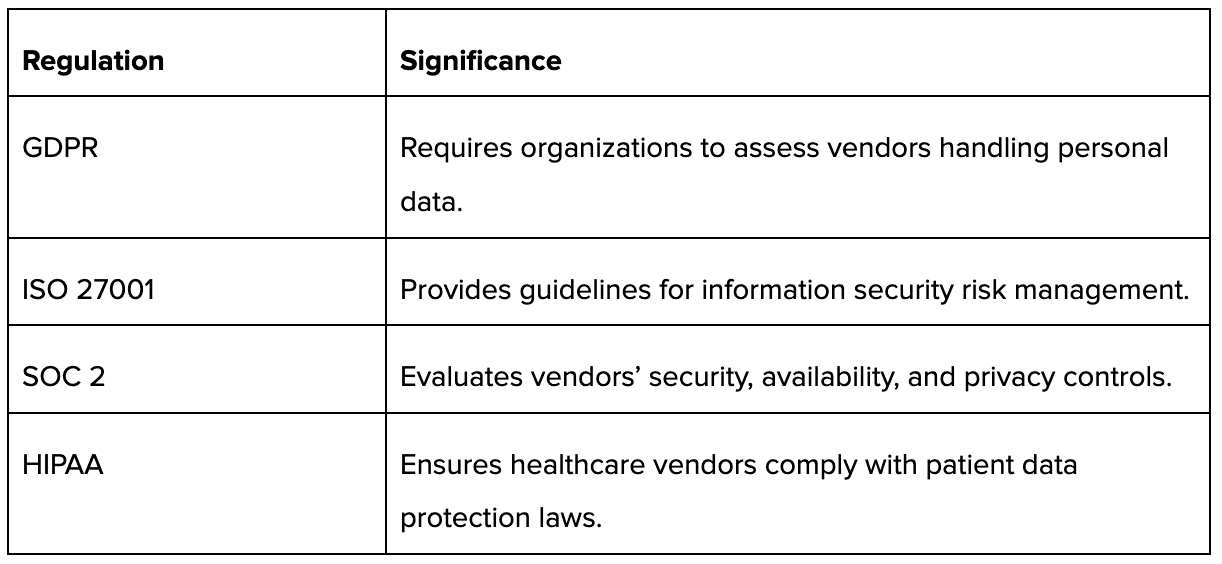
Certain industries mandate periodic vendor assessments to meet standards like GDPR, HIPAA, SOC 2, or ISO 27001. Your business should comply with these regulations to prevent hefty penalties and reputational damages.
By following a clear, step-by-step approach, you can identify potential risks early, take proactive measures, and make informed decisions about vendor relationships. Here’s how to conduct an effective vendor risk assessment:
Start by listing all vendors your company engages with and documenting key details. These should include all the services they provide, the data they access, and their impact on business operations.
Classify vendors into low, medium, or high-risk tiers according to data sensitivity, regulatory requirements, and business impact. It helps prioritize assessment efforts and allocate resources effectively.
Send vendors a structured questionnaire covering critical aspects such as security controls, compliance certifications, financial stability, and operational reliability. After that, review and analyze their responses to identify vulnerabilities and assess potential risks.
Vendor risk management entails the following key categories:
Compile your findings into a vendor risk assessment report that details identified risks, their potential impact, and recommended mitigation strategies. Assign vendor risk scoring based on severity and likelihood and allow stakeholders to make data-driven decisions.
Based on the vendor risk assessment report, determine the next steps, such as
A vendor management risk assessment should reduce third-party risks while ensuring compliance and operational efficiency. Here are the best practices to follow:
Implement third-party risk management (TPRM) software for automating vendor risk analysis, tracking vendor compliance, and generating real-time risk reports. These tools will provide you with a centralized view of potential risks.
A standardized vendor risk analysis framework should ensure uniformity in evaluating third-party vendors. For this, consider defining clear policies that outline the following:
Maintain an up-to-date inventory of all third-party relationships. It will help you track vendor risks effectively and take timely action to address emerging business concerns.
This inventory should include:
To protect sensitive business data, vendors must adhere to recognized security and compliance standards. You should mandate a vendor risk assessment policy with measures like:
You can know more about GDPR compliance services here.
You should continuously monitor vendor performance to identify potential risks before they escalate. Here’s what you should do:
Here are several significant cases that illustrate the consequences of inadequate vendor management and oversight.
1. Morgan Stanley's Data Oversight: Morgan Stanley faced a penalty of $60 million due to inadequate vendor management during the decommissioning of data storage devices.
2. Google and Facebook Invoice Fraud: In a high-profile case from 2019, a Lithuanian man defrauded Google and Facebook of over $100 million through invoice fraud.
3. SolarWinds Cyberattack: In December 2020, SolarWinds was compromised by a sophisticated cyberattack that inserted malware into its software updates. This breach affected around 18,000 customers.
4. Bank of America Third-Party Breach: In 2023, a breach at Infosys McCamish Systems exposed sensitive data for 57,000 Bank of America clients.
A vendor risk assessment policy helps businesses with the following crucial aspects:
The 3rd party risk assessment process requires a structured, proactive approach.
At DPO Consulting, we provide expert guidance and tailored strategies to help businesses strengthen their vendor risk management processes.
Whether you need assistance with compliance frameworks, risk assessments, or ongoing vendor monitoring, our team is here to support you.
Vendor risk refers to potential threats introduced by third-party partnerships that could impact data security, operations, or compliance.
It is used for assessing risks across dimensions such as cybersecurity and finance by assigning scores based on likelihood and impact.
Assessments should be conducted annually or more frequently for high-risk vendors.
It should include cybersecurity policies, compliance documentation, financial stability reports, operational procedures, and reputational checks.
The process should include stakeholders like procurement teams, IT/security personnel, legal advisors, and senior management.
Decisions are based on vendor risk scoring derived from assessment findings; high-risk vendors may require mitigation efforts before approval.
Investing in GDPR compliance efforts can weigh heavily on large corporations as well as smaller to medium-sized enterprises (SMEs). Turning to an external resource or support can relieve the burden of an internal audit on businesses across the board and alleviate the strain on company finances, technological capabilities, and expertise.
External auditors and expert partners like DPO Consulting are well-positioned to help organizations effectively tackle the complex nature of GDPR audits. These trained professionals act as an extension of your team, helping to streamline audit processes, identify areas of improvement, implement necessary changes, and secure compliance with GDPR.
Entrusting the right partner provides the advantage of impartiality and adherence to industry standards and unlocks a wealth of resources such as industry-specific insights, resulting in unbiased assessments and compliance success. Working with DPO Consulting translates to valuable time saved and takes away the burden from in-house staff, while considerably reducing company costs.
GDPR and Compliance
Outsourced DPO & Representation
Training & Support




To give you 100% control over the design, together with Webflow project, you also get the Figma file. After the purchase, simply send us an email to and we will e happy to forward you the Figma file.
Yes, we know... it's easy to say it, but that's the fact. We did put a lot of thought into the template. Trend Trail was designed by an award-winning designer. Layouts you will find in our template are custom made to fit the industry after carefully made research.
We used our best practices to make sure your new website loads fast. All of the images are compressed to have as little size as possible. Whenever possible we used vector formats - the format made for the web.
Grained is optimized to offer a frictionless experience on every screen. No matter how you combine our sections, they will look good on desktop, tablet, and phone.
Both complex and simple animations are an inseparable element of modern website. We created our animations in a way that can be easily reused, even by Webflow beginners.
Our template is modular, meaning you can combine different sections as well as single elements, like buttons, images, etc. with each other without losing on consistency of the design. Long story short, different elements will always look good together.
On top of being modular, Grained was created using the best Webflow techniques, like: global Color Swatches, reusable classes, symbols and more.
Grained includes a blog, carrers and projects collections that are made on the powerful Webflow CMS. This will let you add new content extremely easily.
Grained Template comes with eCommerce set up, so you can start selling your services straight away.
To give you 100% control over the design, together with Webflow project, you also get the Figma file.